Firefox cannot open some sites (sec_error_unknown_issuer)
On a Windows 7 machine, I installed Firefox (40.0.3). When I try to open https://www.google.ch, I get the following error: sec_error_unknown_issuer. There is NO button "I understand the Risks" -- I cannot add an exception. Other sites, like youtube (using https) load without errors. I already deleted the cert8.db file, and the date and time of the machine are also correct.
All Replies (11)
If no issuer chain was provided then certificate is not trusted then it throws an error like sec_error_unknown_issuer then see if you can install this intermediate certificate from another source. You can retrieve the certificate and check details like who issued certificates and expiration dates of certificates. Click the link at the bottom of the error page: "I Understand the Risks" Let Firefox retrieve the certificate: "Add Exception" -> "Get Certificate". Click the "View..." button and inspect the certificate and check who is the issuer of the certificate. You can see more Details like intermediate certificates that are used in the Details pane. If "I Understand the Risks" is missing then this page may be opened in an (i)frame and in that case try the right-click context menu and use "This Frame: Open Frame in New Tab". Note that some firewalls monitor (secure) connections and that programs like Sendori or FiddlerRoot can intercept connections and send their own certificate instead of the website's certificate. Note that it is not recommended to add a permanent exception in cases like this, so only use it to inspect the certificate.
If you have Avast then try to disable HTTPS scanning in Avast Web Shield.
Thanks a lot for your replies. No, there is AVG installed. I also tried to load google using a different machine (running Ubuntu, without antivirus software). I found that this issue also arises there. Further, it is independent of the browser (Chrome and IE also complain about the certificate). Any idea of how to fix this?
Who is the issuer of the certificate?
If you can't inspect the certificate via "I Understand the Risks" then try this:
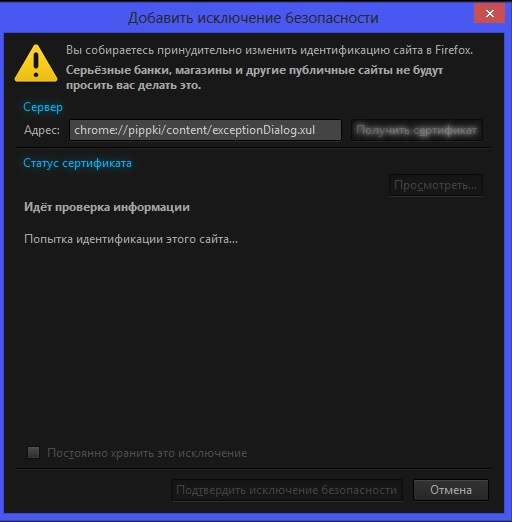
Open the "Add Security Exception" window by pasting this chrome URL in the Firefox location/address bar and check the certificate:
- chrome://pippki/content/exceptionDialog.xul
In the location field of this window type or paste the URL of the website.
- retrieve the certificate via the "Get certificate" button
- click the "View..." button to inspect the certificate in the Certificate Viewer
You can inspect details like the issuer and the certificate chain in the Details tab of the Certificate Viewer. Check who is the issuer of the certificate. If necessary then you can attach a screenshot that shows the certificate viewer.
For me, google.ch uses the same certificate as google.com and youtube.com (for efficiency, Google created a certificate that applies to dozens of domains). You said you can access YouTube. Can you access google.com?
Since this problem affects all browsers, you might have an easier time checking the Issuer and Certificate Hierarchy/Path information in Chrome or IE than in Firefox. Click the slashed-padlock on the address bar, then click the Connection mini-tab, then Certificate Information. What do you find there? I have attached what I see for comparison.
On a Windows 8 machine, I updated Firefox to 43.0.1. When I try to open https://google.com (mail.google.com), I get the following error: sec_error_unknown_issuer. There is NO button "I understand the Risks". Other sites: youtube (using https) load without errors. I already deleted the cert8.db file, and the date and time of the machine are also correct. In IE-browser google.com load without errors. Added certificate google.com/mail.google.com: "Add Exception" -> "Get Certificate" - error :( What me do?
Modified
Hi Anticisco
There is security software like Avast and Kaspersky and BitDefender and ESET that intercepts secure connections and sends their own certificate or that incorporates special web shielding features that can block content.
If you can't inspect the certificate via "I Understand the Risks" then try this:
Open the "Add Security Exception" window by pasting this chrome URL in the Firefox location/address bar and check the certificate:
- chrome://pippki/content/exceptionDialog.xul
In the location field of this window type or paste the URL of the website.
- retrieve the certificate via the "Get certificate" button
- click the "View..." button to inspect the certificate in the Certificate Viewer
You can inspect details like the issuer and the certificate chain in the Details tab of the Certificate Viewer. Check who is the issuer of the certificate. If necessary then you can attach a screenshot that shows the certificate viewer.
cor-el, Antivirus: System Center 2012 EndPoint Protection. Unfortunately, the test certificate Mozilla has not been able to finish (30 minutes working). However, in the "Server" present certificates mail.google.com / google.com before date of 04.14.2016 certificate mail.google.com
You need to paste the URL of the website (https://www.google.com) that you want to check in the location filed of the "Add Security Exception" window (chrome://pippki/content/exceptionDialog.xul window). Your first screenshot shows that you already opened this page and paste the chrome URL another time.
Signature Algorithm Certificate: PKCS # 1 SHA1 With RSA Encryption Issuing Centre: CN = Generic Root CA | C = EN The main limitations of the certificate: Not a CA.
Even after manual installation of the certificate, an error:
- sec_error_cert_signature_algorithm_disabled
(SHA1 oldest algorithm - info from patchnotes MF) The problem was solved after reinstalling the browser to 43.0.4 Thanks for answers %)
Modified
The certificate is not issued by Google as would normally be the case, but is issued by Generic Root CA. So you possibly use a proxy or you have software installed that intercepts this secure connection and sends the Generic Root CA instead to Firefox. A Google search for Generic Root CA doesn't come up with something useful, so I don't know what software or malware this is about.
Boot the computer in Windows Safe Mode with network support (press F8 on the boot screen) to see if that helps.
- http://www.bleepingcomputer.com/tutorials/how-to-start-windows-in-safe-mode/
- http://www.7tutorials.com/4-ways-boot-safe-mode-windows-10
You can use the MSConfig program or the Autoruns utility to see what software is getting started (be cautious with disabling services).
Do a malware check with several malware scanning programs on the Windows computer.
Please scan with all programs because each program detects different malware. All these programs have free versions.
Make sure that you update each program to get the latest version of their databases before doing a scan.
- Malwarebytes' Anti-Malware:
http://www.malwarebytes.org/mbam.php - AdwCleaner:
http://www.bleepingcomputer.com/download/adwcleaner/
http://www.softpedia.com/get/Antivirus/Removal-Tools/AdwCleaner.shtml - SuperAntispyware:
http://www.superantispyware.com/ - Microsoft Safety Scanner:
http://www.microsoft.com/security/scanner/en-us/default.aspx - Windows Defender:
http://windows.microsoft.com/en-us/windows/using-defender - Spybot Search & Destroy:
http://www.safer-networking.org/en/index.html - Kasperky Free Security Scan:
http://www.kaspersky.com/security-scan
You can also do a check for a rootkit infection with TDSSKiller.
- Anti-rootkit utility TDSSKiller:
http://support.kaspersky.com/5350?el=88446
See also:
- "Spyware on Windows": http://kb.mozillazine.org/Popups_not_blocked