CRSF token is making firefox not work in many websites, some examples are: Rancher.io, Splunk.com, Hrblock.ca.
Try to login to Hrblock.ca or any of the website mentioned above.
Chosen solution
It seems both Chrome and Firefox receive the cookie, so I can't think of a reason that both would not generate the same headers running the same script.
To rule out settings, you could try:
New Profile Test
This takes about 3 minutes, plus the time to test the site.
Inside Firefox, type or paste about:profiles in the address bar and press Enter/Return to load it.
Click the Create a New Profile button, then click Next. Assign a name like March2018, ignore the option to relocate the profile folder, and click the Finish button.
After creating the profile, scroll down to it and click the Set as default profile button below that profile, then scroll back up and click the Restart normally button. (There are some other buttons, but please ignore them.)
Firefox should quit and then start up using the new profile, which will just look brand new. If asked whether you want to enable various extensions, ignore those requests for now.
Does the site work any better in the new profile?
When you are done with the experiment, open the about:profiles page again, click the Set as default profile button for your normal profile, then click the Restart normally button to get back to it.
Read this answer in context 👍 1All Replies (7)
I don't understand...
You want to block some sites.
How is this connected with a CSRF token?
What do you want to block, for example, you don't want Firefox to send any requests to those sites, or you don't want Firefox to send any cookies to those sites when you load them, or ???
Modified
Oh, I misread that. Let's start again.
You are trying to log in and you can't. What is the exact error message you're getting?
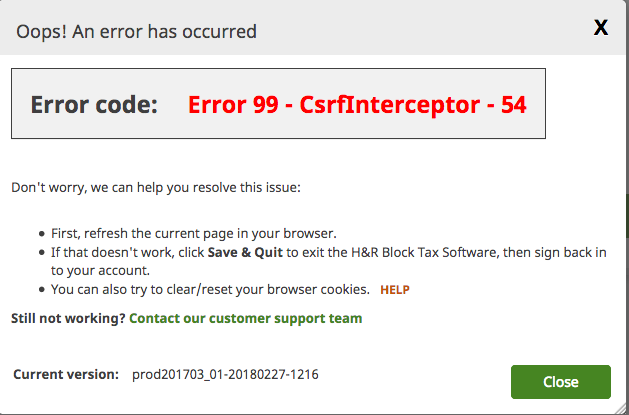
In Hrblock, the show the error "Error 99 - CsrfInterceptor - 54" but I assume is not very meaningful.
Using the console here is the difference between the call Chrome and Firefox are making and I can see that Firefox is not sending the header X-XSRF-TOKEN.
I'll check the other websites and post also the differences if
curl 'https://2017.hrblockonline.ca/hrbweb2017/api/userInfo?userName=email@email' -H 'Host: 2017.hrblockonline.ca' -H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:58.0) Gecko/20100101 Firefox/58.0' -H 'Accept: application/json, text/plain, */*' -H 'Accept-Language: en-US,en;q=0.5' --compressed -H 'If-Modified-Since: Mon, 01 Jan 1990 01:00:00 GMT' -H 'Cache-Control: no-cache' -H 'Referer: https://2017.hrblockonline.ca/?_ga=_ga' -H 'Cookie: SESSION=session; MY_USERID_TOKEN_2015=email@email; XSRF-TOKEN=token' -H 'Connection: keep-alive' -H 'Pragma: no-cache' -H 'DNT: 1'
curl 'https://2017.hrblockonline.ca/hrbweb2017/api/userInfo?userName=email@email' -H 'Pragma: no-cache' -H 'X-XSRF-TOKEN: token' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.9,fr;q=0.8' -H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/64.0.3282.186 Safari/537.36' -H 'Accept: application/json, text/plain, */*' -H 'Cache-Control: no-cache' -H 'Referer: https://2017.hrblockonline.ca/?_ga=ga' -H 'Cookie: SESSION=sesson; optimizelyEndUserId=optimizelyEndUserId; _ga=ga; _gid=gid; _ga=ga; _gid=gid; _tf_v="_tf_v"; __zlcmid=__zlcmid; _tf_u=_tf_u; _uetsid=_uetsid; _gat_UA-29208382-53=1; _gat_UA-26465398-1=1; _tf_s="_tf_s"; XSRF-TOKEN=token' -H 'Connection: keep-alive' -H 'If-Modified-Since: Mon, 01 Jan 1990 01:00:00 GMT' --compressed
PS: I've tried also using Firefox with addons disabled.
Thank you for the request information. This is from the Network Monitor section of the developer tools?
It does seem to be a cross-site request if the current page is on hrblock.ca and the requested resource is on 2017.hrblockonline.ca.
I don't think Firefox constructs that header itself, it would need to be constructed by a script in the page as part of a background request. But could Firefox be stripping it for some reason?
(1) Are you using a private window with Tracking Protection enabled (or a regular window with Tracking Protection enabled)? I don't know whether Tracking Protection would strip that header, but it's worth a test.
(2) Another possible culprit would be an extension. You can view, disable, and often configure or remove extensions on the Add-ons page. Either:
- Command+Shift+a (Windows: Ctrl+Shift+a)
- "3-bar" menu button (or Tools menu) > Add-ons
- type or paste about:addons in the address bar and press Enter/Return
In the left column of the Add-ons page, click Extensions. Then cast a critical eye over the list on the right side. Any extensions Firefox installs for built-in features are hidden from this page, so everything listed here is your choice (and your responsibility) to manage. Anything privacy-related or potentially connection modifying? If in doubt, disable (or remove).
Any improvement?
Thanks for your prompt suggestions!
- This is from the Network Monitor section of the developer tools?
yes, using the developer tools.
- Are you using a private window with Tracking Protection enabled?
Nop, I actually restarted it on safe mode (addons disabled) and tried again having the same results, so the last part shouldn't make any difference.
Let me know if there is anything else I can do. Thanks.
Chosen Solution
It seems both Chrome and Firefox receive the cookie, so I can't think of a reason that both would not generate the same headers running the same script.
To rule out settings, you could try:
New Profile Test
This takes about 3 minutes, plus the time to test the site.
Inside Firefox, type or paste about:profiles in the address bar and press Enter/Return to load it.
Click the Create a New Profile button, then click Next. Assign a name like March2018, ignore the option to relocate the profile folder, and click the Finish button.
After creating the profile, scroll down to it and click the Set as default profile button below that profile, then scroll back up and click the Restart normally button. (There are some other buttons, but please ignore them.)
Firefox should quit and then start up using the new profile, which will just look brand new. If asked whether you want to enable various extensions, ignore those requests for now.
Does the site work any better in the new profile?
When you are done with the experiment, open the about:profiles page again, click the Set as default profile button for your normal profile, then click the Restart normally button to get back to it.
Thanks a lot!!
I guess the addons I'm using are blocking the CSRF header and Disabling the addons does not fully disable them.
Private Badger and Adblock Plus could be the culprits.
Thanks again.