Skype for business web app doesnt work error" Your connection is not secure"
I have been trying to access SFB Web App but I keep getting error: The owner of intweb-xx.xxx.com has configured their website improperly. To protect your information from being stolen, Firefox has not connected to this website. error Code: SEC_ERROR_UNKNOWN_ISSUER
I did follow the steps on the Firefox forum but nothing helped. I deleted the cert8.db file and I add the website https://meet.xx.xxx.com to my exception sites and I even changed the permission to all all i even added intweb-xx.xxx.com to exception list nothing reolsved the issue
please note I am able to access SFB web app in IE and Chrome ONLY Firefox is the one with this issue
Please advice
Chosen solution
I think what that setting does is, in addition to the set of trusted certifidicate issuers included with the product, direct Firefox to use trusted authorities from the Windows certificate store (which is already shared by IE and Chrome). So you're losing a layer of protection caused by Firefox's use of a separate certificate store, but reducing the inconvenience of importing authority certificates on an "as needed" basis.
Read this answer in context 👍 0All Replies (11)
I assume nearly all other HTTPS sites work normally for you without needing exceptions. If you find that you need to make numerous exceptions, there's probably a systemic issue such as a security filter, proxy server, or malware at play.
If other browsers connect without an exception, it may be that the site sends an incomplete certificate chain. In other words, the server is not configured to send one or more intermediate certificates that Firefox needs to verify that the certificate was validly issued.
You can submit the server host name to the following diagnostic page and it will let you know whether there is an incomplete chain, or other issues with the certificate: https://www.ssllabs.com/ssltest/
You also could ask the SFB site whether they are aware of any issues in Firefox and whether THEY can connect using Firefox.
Hi Jscher2000, thank you for your prompt response. i did check the certificate in the site provided and there are nothing flaged and I see the handshake with Firefox 31.3.0 ESR / Win 7 & Firefox 47 / Win 7 R & Firefox 49 / XP SP3 & Firefox 49 / Win 7 R
I dont think its related to the certificate on the hosted site but what else should I be looking for in this report? any suggestions
If you click the Advanced button on the error page, can you click the SEC_ERROR_UNKNOWN_ISSUER code to reveal a coded version of the certificate? I understand you are reluctant to share the address of the problem site here. To see who is the purported issuer of the certificate, you can use a site like the following:
https://certlogik.com/decoder/
Copy from the "-----BEGIN CERTIFICATE-----" through the "-----END CERTIFICATE-----" and paste that into the form and then click Decode.
In the Properties list, under Issuer, does it match what SSLLabs says is the issuer of Certificate #1?
Hi Jscher2000,
/certlogik.com/decoder/ @ certificate summary under property issuer:
CN = Domainname - Enterprise Intermediary CA 1,O = domainname\, Inc.,C = US
but in the SSLLabs says issuer: Symantec Class 3 Secure Server CA - G4
"Enterprise Intermediary CA" sounds like a company proxy server.
Does "Domainname" seem logical for a company proxy server?
I am not sure what you mean by "seems logical for a company proxy server" but "domainname" is correct name for the hosted company
I don't understand why SSLLabs and your Firefox see different certificates. What about in Chrome. Does it show the same issuer as the one Firefox dislikes or the issuer shown on SSLLabs?
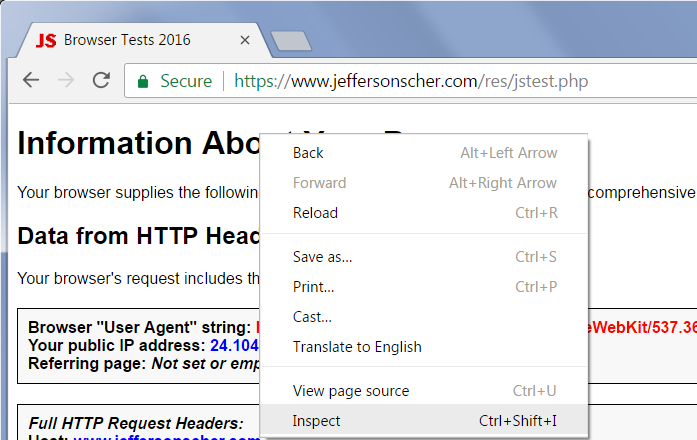
To check that, right-click the page in Chrome and choose Inspect. Then when the developer tools open, click the Security heading to show the panel that has the View Certificate button. Then you can check the issuer shown there.
Ok, I checked chrome as requested and same issuer as certlogik.com/decoder
Issued By:
CN = Domainname - Enterprise Intermediary CA
Only https://www.ssllabs.com/ssltest/ showing different issuer
Assuming that is a legit issuer:
You could try this recently added preference to see whether it helps:
(1) In a new tab, type or paste about:config in the address bar and press Enter/Return. Click the button promising to be careful.
(2) In the search box above the list, type or paste roots and pause while the list is filtered
(3) Double-click the security.enterprise_roots.enabled preference to switch the value from false to true
If that doesn't enable Firefox to trust the intermediary, you can export the certificate from Chrome (really, the Windows certificate viewer dialog) and import it into Firefox as a trusted authority. This post has the typical steps: https://support.mozilla.org/questions/1086078#answer-787652
ok, I change the value for security.enterprise_roots.enabled and it worked. does this will cause any security issue or risk on my machine?
Chosen Solution
I think what that setting does is, in addition to the set of trusted certifidicate issuers included with the product, direct Firefox to use trusted authorities from the Windows certificate store (which is already shared by IE and Chrome). So you're losing a layer of protection caused by Firefox's use of a separate certificate store, but reducing the inconvenience of importing authority certificates on an "as needed" basis.