Security Question-- How to prevent clear-layer screen traps inserted by malware?
While browsing a familiar website named "weather.com", "wunderground" or "intellicast" (all owned by the same corporation), I frequently get false notices to update Firefox or Adobe Flash. The same false notices have appeared on other websites, as well, but not as often.
The false update notice problem is at least one year old, and well-known, but now the same malware uses a new technique to trick unwary users into clicking on its button(s).
The new trick inserts a top-most "clear" layer (a pre-defined area of the screen sensitive to mouse clicks, but not visible to the website visitor), so that when the user attempts to click on any part of a normal visible screen showing through the clear layer, he actually clicks on the intervening, clear layer, itself. With a single misplaced click, the user triggers a bogus pop-up notice to update Firefox or Flash.
If the user is so surprised that he thoughtlessly clicks on the bogus notice's "OK" or other response button, he opens the system to installation of almost any malware, including ransomware.
The clear layer is inserted without any indication it is present, and a mouse-click is the only means to detect its presence. Because the layer is clear, the user has no warning when he clicks on a familiar button showing through the clear layer, and instead of connecting with the intended button, the click brings up the bogus update notice.
The new malware trick is extremely dangerous because users are only one click away from a serious malware infection. Although code which installs the malware is not activated until the user clicks on the malware's bogus response button-- typically labeled "OK"-- the new technique of trapping unwary users surely brings in new victims every day, victims who never understood what happened when they clicked on a simple update notice..
The same new malware also appears in Chrome, as well, but once I realized what must be happening, I stopped testing other browsers to determine vulnerability. Presumably, the malware works on any HTML-reading browser-- only its bogus browser update message changes to suit the context.
Typically, the bogus message concerns a browser or flash update, but today I met a clear-layer pop-up for a dating service, a message completely alien to the host website's standard advertising.
Windows version appears to make no difference, either.
In researching the problem, I have been advised even to change the DNS servers running my TCP/IP protocol. However, that measure makes no difference whatever.
Attempting to recover some degree of security control, I have run system scans to detect any footprint or trace of the malware, but apparently am still clean. But I would rather not wait until a magic bullet is found.
The question, then, is how to deal more effectively with malware which turns the user's own browser into a weapon against the user--
1. Can Firefox be configured to make the HTML code of clear-layer bogus screen messages impossible to read into memory and activate? Rendering a browser unable to read clear-layer code might make some website designers unhappy, but the price for additional protection is worthwhile. (If users are desperate for clear-layered effects, perhaps the browser can be configured to allow them as a manual option.)
2. If insertion of the clear-layer cannot be prevented, can a security challenge be introduced to provide an additional (warning) step, before the clear-layer code response button ("OK") is activated?
3. What else can be done?
Chosen solution
hi, we suspect this is coming form "malvertising" (=ads placed on legitimate websites that redirect you to this fraudulent message), so using an adblocking addon like https://addons.mozilla.org/firefox/addon/ublock-origin/ would also help with that.
Read this answer in context 👍 1All Replies (8)
Chosen Solution
hi, we suspect this is coming form "malvertising" (=ads placed on legitimate websites that redirect you to this fraudulent message), so using an adblocking addon like https://addons.mozilla.org/firefox/addon/ublock-origin/ would also help with that.
alphaa10000 said
Typically, the bogus message concerns a browser or flash update, but today I met a clear-layer pop-up for a dating service, a message completely alien to the host website's standard advertising.
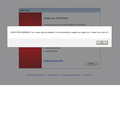
Attached is the latest clear-layer bogus update popup, this for Java. I do not run Java, but most users do not know or care whether Java runs on their system, and are likely to be victimized by this false message.
Thanks, Philipp. In making a reply to thank you, I triggered yet another clear-layer bogus screen. As I clicked on this editor to enter my text, the screen was instantly replaced by an advertisement for a photo service-- not that the image was anything but malware.
Can Firefox be set to block ads effectively without use of a third-party ad blocker? Just a thought, since the FF coders seem focused on the security issue at the moment.
My current settings block pop-up windows, but that configuration may be ineffective against malvertising.
Modified
ok, if this happened while you were here on support.mozilla.org this won't be caused by malvertising (since we don't embed any ads at all), but some form of malware that is already present on your system & a mere adbloker won't help in this case. please perform all the following steps:
- refresh firefox (this will keep your bookmarks and passwords)
- afterwards go to the firefox menu ≡ > addons > extensions and in case there are still extensions listed there, disable them.
- finally run a full scan of your system with different security tools like the free version of malwarebytes and adwcleaner to make sure that adware isn't present in other places of your system as well.
Thanks, Philipp. First, I have decided to confirm my observation, leaving this thread and screen open, waiting for the malvertising screen message to pop up again, all to confirm everything happened as I recall.
1. For that purpose, I have disabled the newly-installed extension UBlock, to permit the bogus screen to appear. Perhaps as measure of its effectiveness, no bogus ads have appeared during any browsing of any site since UBlock's installation.
2. On your question of whether malvertising occurred during a Mozilla forum session, that awaits results of my (open-thread, open-screen) test on the Mozilla forum. Like most users, I customarily have many other tabs open at any time. Although browser focus at the time of attack was on the Mozilla forum URL, there may be something else going on which permits other, previously compromised tabbed URLs to have an influence.
3. Well before I threaded this concern with Mozilla forum, I ran Malwarebytes and another deep scanner for hours, just to be sure, and came up empty (but apparently clear of any malware).
4. I checked my browser \Tools\Options settings for privacy, and left the boxes for "Use Tracking Protection" and apply "Do Not Track" active (checked).
Last, but not least, I am becoming a veteran of the Firefox refresh process, and if the ads persist with UBlock active, then a refresh will be done immediately, followed by a system scan.
Modified
alphaa10000 said
First, I have decided to confirm my observation, leaving this thread and screen open, waiting for the malvertising screen message to pop up again, all to confirm everything happened as I recall. For that purpose, I have disabled the newly-installed extension UBlock, to permit the bogus screen to appear.
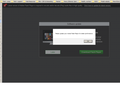
After disabling UBlock, and return to this thread, I clicked on my latest posting to edit something, and ran directly into a clear-layer trap (see screenshot, attached).
If it's like the fake FBI/Interpol browser lock page, This add-on can stop such pages; disallow Script Button {web link} The Disallow Script button looks like a letter "M" and the title is the Minus Script, drag and drop the button on a toolbar. If the button is not displayed then nothing operates, except rules for plugins.
BehindTheOverlay {web link} One click to close any overlay popup on any website. Have you ever been to a website that displays an overlay and masks the content with a transparent background before seeing its content ? This extension allows you to close easily those overlays.
Fred, thank you for those helpful remedies, and I'll review them shortly.
This is a scripting issue, but the remaining puzzle is why clear-layer-traps appear on Mozilla forum, when the Mozilla site runs no embedded ad code, as Philipp explained. I have no reason to doubt this is true, so why do the scripts appear during a Mozilla forum session?
UBlock (the chosen solution from Philipp) works universally to stop scripting behavior, which is why I selected Philipp's answer as the "solution", but I still have no explanation for the need to run UBlock on Mozilla, or face further malvertising screen traps.
Naturally, I am reading background on related topics, but nothing so far. My best guess is something like cross-site scripting is in play, since I have many tabs open at one time, and any of the other, non-Mozilla tabs could come from an infected website. For example, I once frequented the sites weather.com, wunderground.com and intellicast.com-- all from the same (badly managed) web enterprise, "The Weather Company, LLC"-- and these sites are the first locations where the screen traps were observed.
The obvious experiment is to shut down all tabs but Mozilla forum, disable UBlock, and determine once and for all whether the screen traps appear on Mozilla forum. If they do not appear, the scripting must come through other site tabs. The confirmation is to reintroduce the other tabs, perhaps one-at-a-time, and confirm the screen traps reappear. That would be hideously time-consuming, except for the fact the screen-traps appear as though sent after a regular sweep revealed my IP active and still in need of a visit from one.
=================================================
[Written 24 hours later] I have completed the test of Mozilla.org and its forum, and found my screen free of screen-traps after a generous period-- well beyond that usually required to bring attention from malware. Now, I am in-process with reintroduction of tabs, a few at a time, starting with Bleeping Computer, How-to Geek and others.
Modified