How to enable DHE-RSA cipher suite
I enabled dhe-rsa in about:config like the image I attached. But it doesn't have any effect. If I enable other cipher suite like ECDHE it takes effect. Only DHE-RSA does not have any effect. Is it blocked internally or anything? How can I enable DHE-RSA cipher suite.
Chosen solution
Hi zezeon, after further research, these ciphers are not used when TLS 1.3 is enabled, so they seem to have been phased out silently as part of the TLS 1.3 roll-out in bug 1279479.
To see those ciphers on a test page, I needed to disable TLS 1.3 so the initial negotiation was made using TLS 1.2:
security.tls.version.fallback-limit => 3 security.tls.version.max => 3
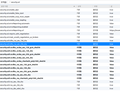
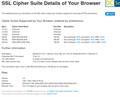
Example screenshots attached using https://www.ssllabs.com/ssltest/viewMyClient.html
That will probably work for a while because TLS 1.2 is still widely deployed.
Read this answer in context 👍 1All Replies (7)
Unfortunately, the image upload failed. Could you try attaching it to a reply?
https://support.mozilla.org/questions/1230259#question-reply
You also could right-click > Copy, then Paste individual preferences from about:config into a reply.
Here is the images
Hmm, possibly because of Logjam the security.ssl3.dhe_rsa_aes_128_sha and security.ssl3.dhe_rsa_aes_256_sha ciphers are not used any more, even though they are listed in preferences??
Is there no way to enable DHE-RSA? I think there would be some way because there is DHE-RSA option in config. Why would they just make a option that doesn't work? Then this is a program malformation. I think such a big project like firefox wouldn't have such a basic fault.
Chosen Solution
Hi zezeon, after further research, these ciphers are not used when TLS 1.3 is enabled, so they seem to have been phased out silently as part of the TLS 1.3 roll-out in bug 1279479.
To see those ciphers on a test page, I needed to disable TLS 1.3 so the initial negotiation was made using TLS 1.2:
security.tls.version.fallback-limit => 3 security.tls.version.max => 3
Example screenshots attached using https://www.ssllabs.com/ssltest/viewMyClient.html
That will probably work for a while because TLS 1.2 is still widely deployed.
See also: bug 1169721 - ssl_error_weak_server_ephemeral_dh_key - TLS_DHE_RSA_WITH_AES_128_CBC_SHA listed in TLS handshake supported ciphers, but not actually supported.
Thanks jscher2000.. You saved me. Limiting tls version worked. For a long time I was not able to test my software, because no browser is supporting DHE-RSA(suddenly). Now I can move forward.. cor-el, thanks too.