self-signed certificate in IIS 7.5
Hello, We are getting the "Secure Connection Failed" when browsing to an internal site with an SSL certificate that was self-signed by the server. There is no way to add it to a safe list or bypass security to get around it. Is there anything I can do to avoid this? We aren't looking to purchase an outside cert just for our internal site. This is version 36.0.4. Thanks! -Dusty
Chosen solution
Turns out it was the TLS_RSA_WITH_3DES_EDE_CBC_SHA cipher that needed to be added back in. It appears to be working fine now.
Read this answer in context 👍 0All Replies (5)
hello, is there any particular error code shown on the page?
Yep:
Secure Connection Failed
The connection to the server was reset while the page was loading.
- The page you are trying to view cannot be shown because the authenticity of the received data could not be verified.
- Please contact the website owners to inform them of this problem.
My options are to try again or report the error. This works on every other browser and worked before 36.0.1.
this probably won't be a general issue with self-signed certificates but something particular that is out of order. maybe check that the internal server isn't only offering a rc4 encryption cipher suite or uses SSL 3.0 exclusively: https://developer.mozilla.org/en-US/Firefox/Releases/36/Site_Compatibility#Security
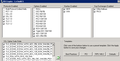
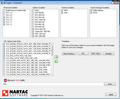
I've attached an image of IIS Crypto. The were put in place for our Mercurial site to best perform.
From what you're saying SSL 3.0 shouldn't be used or it shouldn't be the only one? We had turned of 2.0 due to some issues with Mercurial.
Another funny thing: when connecting to the site through VPN on a non-domain PC, I'm able to get in the site like I used to prior to 36.0.1.
Chosen Solution
Turns out it was the TLS_RSA_WITH_3DES_EDE_CBC_SHA cipher that needed to be added back in. It appears to be working fine now.