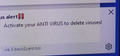
Getting pop-up for critical virus alert when running 96.0.3 on Win 10 Pro
I'm running 96.0.3 on a fully patched Win 10 Pro system - both O/S and programs. When Firefox is running I'm getting these pop-up error messages randomly with changing content. They stay on screen for some seconds and then go away. Message states it's from (via) 5.back2yard.biz. I put that in my hosts file and I'm still getting them. My network is a cable modem hooked to Xfinity and then cable connected to another fully newer patched router. All addresses are 10. range. I ran both a Malwarebytes scan and a Windows Security scan - both are clean.
I'm unable to upload a small image after a hour so I'll give up on that right now.
Chosen solution
Did several scans with no findings. There weren't any add-ons. I gave in to the virus gods and did a Windows uninstall and delete in %appdata%. After a reinstall from the full download I'm not getting any more pop-ups and the system is still clean.
Thanks for your time. FF is my 99% browser.
Read this answer in context 👍 1All Replies (18)
Funny - was able to upload the image with Post a Reply.
Whenever you get a message / popup like that;
DO NOT USE ANY OF THE PROVIDED LINKS OR ANY PHONE NUMBERS ! !
Such messages are only Spam that could lead you to Fake Support. Not only can they damage or hack your system, they charge you to do so.
You can report such a site at; http://www.google.com/safebrowsing/report_phish/ Google Report Phishing Page which is the same when done while on site by going to Help > Report Web Forgery
http://www.mozilla.org/en-US/legal/fraud-report/ Help us safeguard Mozilla’s trademarks by reporting misuse
https://support.mozilla.org/en-US/kb/avoid-and-report-mozilla-tech-support-scams
You may have ad/mal-ware. Further information can be found in this article; https://support.mozilla.org/en-US/kb/troubleshoot-firefox-issues-caused-malware?cache=no
Run most or all of the listed free to use malware scanners. Each works differently. If one program misses something, another may pick it up.
Go to the Mozilla Add-ons Web Page {web Link} (There’s a lot of good stuff here) and search for a good ad blocker.
I'm no stranger to scam pop-ups but this one is different.
Firefox is on the Google main search page: https://www.google.com/
I doubt the Google is hacked. I did put the purported site into my hosts file so they are using some other URL.
Many websites have been hacked over the years. There IT's don't know this until they are told. Also, remember the unwanted messages might not have come from that site. But report it to them just the same.
I did install StopAll Ads. I'll leave it enabled all the time except for financial website and checking email unless I can find where a knowledgeable party has done packet reviews and/or other detailed work to see what it might send (if anything).
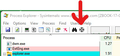
I would use Process Explorer to see what process is driving that alert. https://docs.microsoft.com/en-us/sysinternals/downloads/process-explorer
Just click and hold the bullseye and let go over that popup to see what process is driving it. see screenshot
I uninstalled the blocker. Set up windows firewall and for all profiles I'm logging inbound connections. Even with the system just sitting there with Firefox just on Google lots of activity. I think I'll need to actually see the pop-up and get the time to make any sense out it. Should I just use my own website on Weebly?
Haven't used sysinternals for years since I'm mostly retired. Have on the system and I'll just start it so if I see the pop-up can quickly go over it.
I managed to catch the pop-up. Process Explorer went to firefox - see pic. I don't know the exact second but the firewall log shows traffic including 239.255.255.250 at 1:06PM EST - no idea why or where this IP is located. Next time I'm just going to do a reboot right away to perhaps get a better idea.
Here's the firewall log with the lead entry and then from 1:05 to 1:07EST. My clock showed 1:06 with the pop-up. I masked the 10. network info just in case that would help some from the outside - which I seriously doubt but I'm retired and not getting training anymore. 10.XX.YY.ZZ is the workstation and 10.XX.YY.1 is the router.
- Version: 1.5
- Software: Microsoft Windows Firewall
- Time Format: Local
- Fields: date time action protocol src-ip dst-ip src-port dst-port size tcpflags tcpsyn tcpack tcpwin icmptype icmpcode info path
2022-02-06 11:23:17 ALLOW TCP 127.0.0.1 127.0.0.1 54561 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:05:00 ALLOW 2 10.XX.YY.ZZ 224.0.0.251 - - 0 - - - - - - - SEND
2022-02-06 13:05:00 ALLOW 2 10.XX.YY.ZZ 224.0.0.251 - - 0 - - - - - - - RECEIVE
2022-02-06 13:05:30 ALLOW TCP 127.0.0.1 127.0.0.1 50688 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:05:30 ALLOW TCP 127.0.0.1 127.0.0.1 50688 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:05:49 ALLOW TCP 127.0.0.1 127.0.0.1 50689 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:05:49 ALLOW TCP 127.0.0.1 127.0.0.1 50689 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:05:49 ALLOW TCP 127.0.0.1 127.0.0.1 50690 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:05:49 ALLOW TCP 127.0.0.1 127.0.0.1 50690 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:14 ALLOW TCP 127.0.0.1 127.0.0.1 50691 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:14 ALLOW TCP 127.0.0.1 127.0.0.1 50691 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:16 ALLOW UDP 192.168.56.1 239.255.255.250 52072 1900 0 - - - - - - - SEND
2022-02-06 13:06:16 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 52073 1900 0 - - - - - - - SEND
2022-02-06 13:06:16 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 52073 1900 0 - - - - - - - RECEIVE
2022-02-06 13:06:17 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 52073 1900 0 - - - - - - - RECEIVE
2022-02-06 13:06:18 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 52073 1900 0 - - - - - - - RECEIVE
2022-02-06 13:06:19 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 52073 1900 0 - - - - - - - RECEIVE
2022-02-06 13:06:22 ALLOW UDP 10.XX.YY.ZZ 8.8.8.8 63523 53 0 - - - - - - - SEND
2022-02-06 13:06:22 ALLOW UDP 10.XX.YY.ZZ 10.XX.YY.1 63523 53 0 - - - - - - - SEND
2022-02-06 13:06:22 ALLOW UDP 10.XX.YY.ZZ 8.8.8.8 63040 53 0 - - - - - - - SEND
2022-02-06 13:06:22 ALLOW UDP 10.XX.YY.ZZ 10.XX.YY.1 63040 53 0 - - - - - - - SEND
2022-02-06 13:06:22 ALLOW TCP 10.XX.YY.ZZ 62.210.6.153 50692 443 0 - 0 0 0 - - - SEND
2022-02-06 13:06:23 ALLOW TCP 10.XX.YY.ZZ 46.4.18.135 50693 443 0 - 0 0 0 - - - SEND
2022-02-06 13:06:23 ALLOW TCP 127.0.0.1 127.0.0.1 50695 50694 0 - 0 0 0 - - - SEND
2022-02-06 13:06:23 ALLOW TCP 127.0.0.1 127.0.0.1 50695 50694 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:23 ALLOW TCP 10.XX.YY.ZZ 23.62.152.74 50696 80 0 - 0 0 0 - - - SEND
2022-02-06 13:06:23 ALLOW TCP 127.0.0.1 127.0.0.1 50697 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:23 ALLOW TCP 127.0.0.1 127.0.0.1 50697 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:23 ALLOW TCP 127.0.0.1 127.0.0.1 50698 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:23 ALLOW TCP 127.0.0.1 127.0.0.1 50698 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:23 ALLOW TCP 127.0.0.1 127.0.0.1 50699 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:23 ALLOW TCP 127.0.0.1 127.0.0.1 50699 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:30 ALLOW TCP 127.0.0.1 127.0.0.1 50700 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:30 ALLOW TCP 127.0.0.1 127.0.0.1 50700 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:36 ALLOW TCP 10.XX.YY.ZZ 34.120.208.123 50701 443 0 - 0 0 0 - - - SEND
2022-02-06 13:06:45 ALLOW TCP 127.0.0.1 127.0.0.1 50702 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:45 ALLOW TCP 127.0.0.1 127.0.0.1 50702 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:46 ALLOW TCP 127.0.0.1 127.0.0.1 50703 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:46 ALLOW TCP 127.0.0.1 127.0.0.1 50703 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:47 ALLOW TCP 127.0.0.1 127.0.0.1 50704 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:47 ALLOW TCP 127.0.0.1 127.0.0.1 50704 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:47 ALLOW TCP 127.0.0.1 127.0.0.1 50705 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:47 ALLOW TCP 127.0.0.1 127.0.0.1 50705 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:47 ALLOW TCP 127.0.0.1 127.0.0.1 50706 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:47 ALLOW TCP 127.0.0.1 127.0.0.1 50706 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:47 ALLOW TCP 127.0.0.1 127.0.0.1 50707 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:47 ALLOW TCP 127.0.0.1 127.0.0.1 50707 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:47 ALLOW TCP 127.0.0.1 127.0.0.1 50708 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:47 ALLOW TCP 127.0.0.1 127.0.0.1 50708 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:49 ALLOW TCP 10.XX.YY.ZZ 51.104.167.255 50709 443 0 - 0 0 0 - - - SEND
2022-02-06 13:06:53 ALLOW TCP 127.0.0.1 127.0.0.1 50710 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:53 ALLOW TCP 127.0.0.1 127.0.0.1 50710 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:55 ALLOW TCP 127.0.0.1 127.0.0.1 50711 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:55 ALLOW TCP 127.0.0.1 127.0.0.1 50711 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:06:55 ALLOW TCP 127.0.0.1 127.0.0.1 50712 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:06:55 ALLOW TCP 127.0.0.1 127.0.0.1 50712 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:07:09 ALLOW 2 10.XX.YY.ZZ 239.255.255.250 - - 0 - - - - - - - SEND
2022-02-06 13:07:09 ALLOW 2 10.XX.YY.ZZ 239.255.255.250 - - 0 - - - - - - - RECEIVE
2022-02-06 13:07:16 ALLOW TCP 127.0.0.1 127.0.0.1 50713 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:07:16 ALLOW TCP 127.0.0.1 127.0.0.1 50713 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:07:24 ALLOW UDP 10.XX.YY.ZZ 8.8.8.8 61581 53 0 - - - - - - - SEND
2022-02-06 13:07:24 ALLOW UDP 10.XX.YY.ZZ 10.XX.YY.1 61581 53 0 - - - - - - - SEND
2022-02-06 13:07:24 ALLOW UDP 10.XX.YY.ZZ 8.8.8.8 59084 53 0 - - - - - - - SEND
2022-02-06 13:07:24 ALLOW UDP 10.XX.YY.ZZ 10.XX.YY.1 59084 53 0 - - - - - - - SEND
2022-02-06 13:07:24 ALLOW TCP 10.XX.YY.ZZ 172.217.15.195 50715 443 0 - 0 0 0 - - - SEND
2022-02-06 13:07:24 ALLOW TCP 10.XX.YY.ZZ 172.217.165.206 50718 443 0 - 0 0 0 - - - SEND
2022-02-06 13:07:28 ALLOW TCP 10.XX.YY.ZZ 34.117.237.239 50719 443 0 - 0 0 0 - - - SEND
2022-02-06 13:07:28 ALLOW TCP 10.XX.YY.ZZ 62.210.6.153 50720 443 0 - 0 0 0 - - - SEND
2022-02-06 13:07:29 ALLOW TCP 127.0.0.1 127.0.0.1 50722 50721 0 - 0 0 0 - - - SEND
2022-02-06 13:07:29 ALLOW TCP 127.0.0.1 127.0.0.1 50722 50721 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:07:31 ALLOW TCP 127.0.0.1 127.0.0.1 50723 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:07:31 ALLOW TCP 127.0.0.1 127.0.0.1 50723 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:07:36 ALLOW TCP 127.0.0.1 127.0.0.1 50724 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:07:36 ALLOW TCP 127.0.0.1 127.0.0.1 50724 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 13:07:55 ALLOW TCP 127.0.0.1 127.0.0.1 50725 49350 0 - 0 0 0 - - - SEND
2022-02-06 13:07:55 ALLOW TCP 127.0.0.1 127.0.0.1 50725 49350 0 - 0 0 0 - - - RECEIVE
I called for more help.
I caught some more masked my local 10. IPs. Each of these have that same IP address. I'm going to reset firewall logging and install wireshark since I used previously for really hard problems.
2022-02-07 11:20:04 ALLOW UDP 192.168.56.1 239.255.255.250 59522 1900 0 - - - - - - - SEND 2022-02-07 11:20:04 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 59523 1900 0 - - - - - - - SEND 2022-02-07 11:20:04 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 59523 1900 0 - - - - - - - RECEIVE 2022-02-07 11:20:05 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 59523 1900 0 - - - - - - - RECEIVE 2022-02-07 11:20:06 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 59523 1900 0 - - - - - - - RECEIVE 2022-02-07 11:20:07 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 59523 1900 0 - - - - - - - RECEIVE 2022-02-07 11:20:07 ALLOW TCP 127.0.0.1 127.0.0.1 50244 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:07 ALLOW TCP 127.0.0.1 127.0.0.1 50244 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:07 ALLOW TCP 127.0.0.1 127.0.0.1 50245 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:07 ALLOW TCP 127.0.0.1 127.0.0.1 50245 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:08 ALLOW UDP 10.XX.YY.ZZ 8.8.8.8 63368 53 0 - - - - - - - SEND 2022-02-07 11:20:08 ALLOW TCP 10.XX.YY.ZZ 13.69.109.130 50246 443 0 - 0 0 0 - - - SEND 2022-02-07 11:20:08 ALLOW TCP 127.0.0.1 127.0.0.1 50247 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:08 ALLOW TCP 127.0.0.1 127.0.0.1 50247 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:08 ALLOW TCP 127.0.0.1 127.0.0.1 50248 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:08 ALLOW TCP 127.0.0.1 127.0.0.1 50248 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:08 ALLOW TCP 127.0.0.1 127.0.0.1 50249 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:08 ALLOW TCP 127.0.0.1 127.0.0.1 50249 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:10 ALLOW TCP 127.0.0.1 127.0.0.1 50250 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:10 ALLOW TCP 127.0.0.1 127.0.0.1 50250 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:10 ALLOW TCP 127.0.0.1 127.0.0.1 50251 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:10 ALLOW TCP 127.0.0.1 127.0.0.1 50251 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:12 ALLOW TCP 127.0.0.1 127.0.0.1 50252 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:12 ALLOW TCP 127.0.0.1 127.0.0.1 50252 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:12 ALLOW TCP 127.0.0.1 127.0.0.1 50253 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:12 ALLOW TCP 127.0.0.1 127.0.0.1 50253 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:24 ALLOW 2 10.XX.YY.ZZ 224.0.0.252 - - 0 - - - - - - - SEND 2022-02-07 11:20:24 ALLOW 2 10.XX.YY.ZZ 224.0.0.252 - - 0 - - - - - - - RECEIVE 2022-02-07 11:20:25 ALLOW TCP 127.0.0.1 127.0.0.1 50254 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:25 ALLOW TCP 127.0.0.1 127.0.0.1 50254 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:25 ALLOW TCP 127.0.0.1 127.0.0.1 50255 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:25 ALLOW TCP 127.0.0.1 127.0.0.1 50255 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:25 ALLOW TCP 127.0.0.1 127.0.0.1 50256 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:25 ALLOW TCP 127.0.0.1 127.0.0.1 50256 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:25 ALLOW TCP 127.0.0.1 127.0.0.1 50257 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:25 ALLOW TCP 127.0.0.1 127.0.0.1 50257 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:25 ALLOW TCP 127.0.0.1 127.0.0.1 50258 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:25 ALLOW TCP 127.0.0.1 127.0.0.1 50258 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:50 ALLOW TCP 127.0.0.1 127.0.0.1 50259 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:50 ALLOW TCP 127.0.0.1 127.0.0.1 50259 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:50 ALLOW TCP 127.0.0.1 127.0.0.1 50260 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:50 ALLOW TCP 127.0.0.1 127.0.0.1 50260 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:51 ALLOW TCP 127.0.0.1 127.0.0.1 50261 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:51 ALLOW TCP 127.0.0.1 127.0.0.1 50261 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:51 ALLOW TCP 127.0.0.1 127.0.0.1 50262 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:51 ALLOW TCP 127.0.0.1 127.0.0.1 50262 49350 0 - 0 0 0 - - - RECEIVE 2022-02-07 11:20:55 ALLOW TCP 127.0.0.1 127.0.0.1 50263 49350 0 - 0 0 0 - - - SEND 2022-02-07 11:20:55 ALLOW TCP 127.0.0.1 127.0.0.1 50263 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 11:34:11 ALLOW TCP 127.0.0.1 127.0.0.1 49974 49350 0 - 0 0 0 - - - SEND
2022-02-06 11:34:11 ALLOW TCP 127.0.0.1 127.0.0.1 49974 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 11:34:16 ALLOW UDP 192.168.56.1 239.255.255.250 61847 1900 0 - - - - - - - SEND
2022-02-06 11:34:16 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 61848 1900 0 - - - - - - - SEND
2022-02-06 11:34:16 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 61848 1900 0 - - - - - - - RECEIVE
2022-02-06 11:34:16 ALLOW UDP 10.XX.YY.ZZ 10.XX.YY.1 137 137 0 - - - - - - - SEND
2022-02-06 11:34:17 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 61848 1900 0 - - - - - - - RECEIVE
2022-02-06 11:34:18 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 61848 1900 0 - - - - - - - RECEIVE
2022-02-06 11:34:19 ALLOW UDP 10.XX.YY.ZZ 239.255.255.250 61848 1900 0 - - - - - - - RECEIVE
2022-02-06 11:34:22 ALLOW TCP 127.0.0.1 127.0.0.1 49975 49350 0 - 0 0 0 - - - SEND
2022-02-06 11:34:22 ALLOW TCP 127.0.0.1 127.0.0.1 49975 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 11:34:22 ALLOW TCP 127.0.0.1 127.0.0.1 49976 49350 0 - 0 0 0 - - - SEND
2022-02-06 11:34:22 ALLOW TCP 127.0.0.1 127.0.0.1 49976 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 11:34:23 ALLOW TCP 127.0.0.1 127.0.0.1 49977 49350 0 - 0 0 0 - - - SEND
2022-02-06 11:34:23 ALLOW TCP 127.0.0.1 127.0.0.1 49977 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 11:34:31 ALLOW TCP 127.0.0.1 127.0.0.1 49978 49350 0 - 0 0 0 - - - SEND
2022-02-06 11:34:31 ALLOW TCP 127.0.0.1 127.0.0.1 49978 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 11:34:34 ALLOW TCP 127.0.0.1 127.0.0.1 49979 49350 0 - 0 0 0 - - - SEND
2022-02-06 11:34:34 ALLOW TCP 127.0.0.1 127.0.0.1 49979 49350 0 - 0 0 0 - - - RECEIVE
2022-02-06 11:34:55 ALLOW 2 10.XX.YY.ZZ 239.255.255.250 - - 0 - - - - - - - SEND
2022-02-06 11:34:55 ALLOW 2 10.XX.YY.ZZ 239.255.255.250 - - 0 - - - - - - - RECEIVE
Found that that 239.255.255.250 is used by Simple Service Discovery Protocol. Per Wikipedia it's the basis for UPnP. Also "The network company Cloudflare has described this attack as the "Stupidly Simple DDoS Protocol"". Also "Firefox for Android prior to version 79 did not properly validate the schema of the URL" - but that's Android and I'm on Win 10 Pro.
I just double-checked the router and UPnP is turned OFF.
I started FF up and the pop-ups immediately started. Closed FF while they were still up and then one disappeared and then the other three. Is something hitch hiking on FF just to get into the system?
On my post: https://support.mozilla.org/en-US/questions/1366882#answer-1480888 I said to check for malware using the listed programs. Have you done so?
Seburo said
Hi Fred. My first thought would be to clear the browsing history. If that does not work, try a new profile without any add-ons.
Use these links to create a new profile. Use this new profile as is. Is the problem still there?
https://support.mozilla.org/en-US/kb/how-run-firefox-when-profile-missing-inaccessible
http://kb.mozillazine.org/Profile_folder_-_Firefox#Navigating_to_the_profile_folder
https://support.mozilla.org/en-US/kb/profile-manager-create-and-remove-firefox-profiles
https://support.mozilla.org/en-US/kb/back-and-restore-information-firefox-profiles
Type about:profiles<enter> in the address box.
Chosen Solution
Did several scans with no findings. There weren't any add-ons. I gave in to the virus gods and did a Windows uninstall and delete in %appdata%. After a reinstall from the full download I'm not getting any more pop-ups and the system is still clean.
Thanks for your time. FF is my 99% browser.
Sorry for the late reply. Been in Hospital.
That was very good work. Well Done.