mozilla.cfg not applying
C:\Program Files (x86)\Mozilla Firefox\mozilla.cfg
C:\Program Files (x86)\Mozilla Firefox\Override.ini C:\Program Files (x86)\Mozilla Firefox\local-setting.js
I can't get the mozilla.cfg file to apply. I went simple and just put app.update.enable in there. I went back from 40.0.3 to 40.0.2. I have tried saving the files in UTF-8. I ensured that the file extensions are correct. I am at the end of my rope. Here are the pics of the file contents.
All Replies (11)
hi, as per http://kb.mozillazine.org/Locking_preferences please try to save those files ANSI-encoded...
Thanks for the help.
They are now and originally were. I tried UTF-8 as a troubleshooting step. ANSI makes no difference.
actually local-setting.js should go into "C:\Program Files (x86)\Mozilla Firefox\defaults\pref"
You need to place a local-settings.js file in the defaults\pref folder where also the channel-prefs.js file is located to specify using mozilla.cfg.
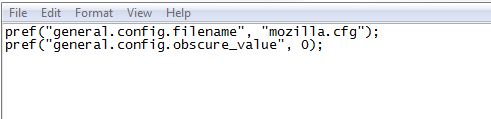
pref("general.config.filename", "mozilla.cfg");
pref("general.config.obscure_value", 0);
These functions can be used in the mozilla.cfg file:
defaultPref(); // set new default value pref(); // set pref, allow changes in current session lockPref(); // lock pref, disallow changes
See:
The file name is override.ini with a lowercase 'O'.
Yes, that was a typo. I hand jammed the destination.
Is it true that if there is one error in the Mozilla.cfg file that the whole thing won't work?
Yes. The mozilla.cfg file is run as a JavaScript and not interpreted like the prefs.js and user.js files. Any error in the file throws an exception and abort the execution.
This also means that you can place all kind on JavaScript in the file that runs with chrome privileges. You can also use try and catch blocks as a test to see if things work or comment out lines with a starting //.
Yes, I read all that an d that is how I got here.
Now, I went back to 40.0.2 and resaved the files and now app.update.enabled says false. YAY.
But then this doesn't work:
//
lockPref("browser.startup.homepage", "https://www.google.com");
lockpref("browser.download.useDownloadDir", false);
lockPref("app.update.enabled", false);
lockPref("extensions.update.enabled", false);
lockPref("browser.shell.checkDefaultBrowser", false);
lockPref("browser.search.update", false);
lockPref("browser.formfill.enable", false);
lockPref("signon.autofillForms", false);
lockPref("dom.disable_open_during_load", true);
lockPref("dom.disable_window_move_resize", true);
lockPref("dom.event.contextmenu.enabled", false);
lockPref("dom.disable_window_status_change", true);
lockPref("dom.disable_window_flip", true);
lockPref("dom.disable_window_open_feature.status", true);
lockPref("privacy.sanitize.sanitizeOnShutdown", true);
lockPref("security.default_personal_cert", "Ask Every Time");
lockPref("signon.rememberSignons", false);
lockPref("xpinstall.whitelist.required", true);
lockPref("network.protocol-handler.external.shell",false);
lockPref("security.ssl3.dhe_rsa_aes_128_sha;true",true);
lockPref("security.ssl3.dhe_rsa_aes_256_sha;true",true);
lockPref("security.ssl3.ecdhe_ecdsa_aes_128_gcm_sha256;true",true);
lockPref("security.ssl3.ecdhe_ecdsa_aes_128_sha;true",true);
lockPref("security.ssl3.ecdhe_ecdsa_aes_256_sha;true",true);
lockPref("security.ssl3.ecdhe_ecdsa_rc4_128_sha;true",true);
lockPref("security.ssl3.ecdhe_rsa_aes_128_gcm_sha256;true",true);
lockPref("security.ssl3.ecdhe_rsa_aes_128_sha;true",true);
lockPref("security.ssl3.ecdhe_rsa_aes_256_sha;true",true);
lockPref("security.ssl3.ecdhe_rsa_rc4_128_sha;true",true);
lockPref("security.ssl3.rsa_aes_128_sha;true",true);
lockPref("security.ssl3.rsa_aes_256_sha;true",true);
lockPref("security.ssl3.rsa_des_ede3_sha;true",true);
lockPref("security.ssl3.rsa_rc4_128_md5;true",true);
lockPref("security.ssl3.rsa_rc4_128_sha;true",true);
pref("toolkit.telemetry.unifiedIsOptIn", false);
pref("toolkit.telemetry.enabled", false);
Anything pop out at you?
HAHAHA I see it...:true" true
What was I thinking...let me see if it works.
Nope, I am going to have to go through each line. None of the settings apply.
Yes, that won't work :wink:
Any special reason to set these to true? Those were disabled because of the logjan vulnerability.
- security.ssl3.dhe_rsa_aes_128_sha
- security.ssl3.dhe_rsa_aes_256_sha
Locking this pref will prevent users from getting a special context menu on web pages, so you may want to reconsider and use pref() instead to only initialize the pref. lockPref("dom.event.contextmenu.enabled", false);
Hmm, I'm not sure how I missed this lockpref instead of lockPref:
lockpref("browser.download.useDownloadDir", false);
lockPref("browser.download.useDownloadDir", false);
//
lockPref("browser.startup.homepage", "https://www.google.com");
lockPref("browser.download.useDownloadDir", false);
lockPref("app.update.enabled", false);
lockPref("extensions.update.enabled", false);
lockPref("browser.shell.checkDefaultBrowser", false);
lockPref("browser.search.update", false);
lockPref("browser.formfill.enable", false);
lockPref("signon.autofillForms", false);
lockPref("dom.disable_open_during_load", true);
lockPref("dom.disable_window_move_resize", true);
lockPref("dom.event.contextmenu.enabled", false);
lockPref("dom.disable_window_status_change", true);
lockPref("dom.disable_window_flip", true);
lockPref("dom.disable_window_open_feature.status", true);
lockPref("privacy.sanitize.sanitizeOnShutdown", true);
lockPref("security.default_personal_cert", "Ask Every Time");
lockPref("signon.rememberSignons", false);
lockPref("xpinstall.whitelist.required", true);
lockPref("network.protocol-handler.external.shell",false);
lockPref("security.ssl3.dhe_rsa_aes_128_sha",true);
lockPref("security.ssl3.dhe_rsa_aes_256_sha",true);
lockPref("security.ssl3.ecdhe_ecdsa_aes_128_gcm_sha256",true);
lockPref("security.ssl3.ecdhe_ecdsa_aes_128_sha",true);
lockPref("security.ssl3.ecdhe_ecdsa_aes_256_sha",true);
lockPref("security.ssl3.ecdhe_ecdsa_rc4_128_sha",true);
lockPref("security.ssl3.ecdhe_rsa_aes_128_gcm_sha256",true);
lockPref("security.ssl3.ecdhe_rsa_aes_128_sha",true);
lockPref("security.ssl3.ecdhe_rsa_aes_256_sha",true);
lockPref("security.ssl3.ecdhe_rsa_rc4_128_sha",true);
lockPref("security.ssl3.rsa_aes_128_sha",true);
lockPref("security.ssl3.rsa_aes_256_sha",true);
lockPref("security.ssl3.rsa_des_ede3_sha",true);
lockPref("security.ssl3.rsa_rc4_128_md5",true);
lockPref("security.ssl3.rsa_rc4_128_sha",true);
pref("toolkit.telemetry.unifiedIsOptIn", false);
pref("toolkit.telemetry.enabled", false);
Modified