Since FF 78.0, we cannot access self-signed certificate sites due to HSTS
The issue described here does not affect version 77.0.1 and earlier, only 78.0 and later.
Update: Wrote an complete analysis on this as HSTS for human beings HSTS for human beings
So, we have a number of internal sites employing a self-signed certificate with a CN not matching the hostname. As an example of such devices are HP iLOs, switches and a series of others that are now completely inaccebile through Firefox.
Up until version 77.0.1, we were getting the usual notofication about the two issues (not trusted and cn is wrong) but we could Add an exception and proceed.
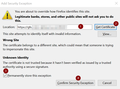
After updating to version 78.0, proceeding is not offered as an option, due to HSTS requirments.
hostname.com has a security policy called HTTP Strict Transport Security (HSTS), which means that Firefox can only connect to it securely. You can’t add an exception to visit this site.
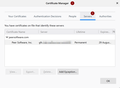
Troubleshooting done already; Completely deleted everything (FF and profiles and start clean - same issue Renamed SiteSecurityServiceState.txt so FF can create a new one - same issue Imported the certificate into Firefox as an exception manually as per images attached - same issue
At this point, there is no way to access those sites no matter what we have done and the issue persists up to the latest current version of the browser.
Just as a hint, the same issue appeared the same period of time (during the summer) on Chrome and Chromium Edge.
Modified
Chosen solution
Finally found the root cause!
So, our domain was recently added to the list including subdomains. So, there you go, this is what happens when you do that. All and any subdomain is then considered HSTS enforced by all browsers.
Good thing for Firefox to have that workaround so developers don't get crazy. Unfortunately, no such workaround exists for the chromium browsers.
Read this answer in context 👍 0All Replies (4)
On Chrome, the issues appeared after updating from 84.0 to 85.0
Found a way to fix it! Kill HSTS.
about:config network.stricttransportsecurity.preloadlist = false
Mozilla uses Google's list for the preload list, so it's understandable that disabling the list would help. But why is the domain on Google's list in the first place? Hmm...
Chosen Solution
Finally found the root cause!
So, our domain was recently added to the list including subdomains. So, there you go, this is what happens when you do that. All and any subdomain is then considered HSTS enforced by all browsers.
Good thing for Firefox to have that workaround so developers don't get crazy. Unfortunately, no such workaround exists for the chromium browsers.