Adding an internal range to firefox intune policy management for access control
Hi All, I want to block traffic on firefox externally for managed devices via Intune, following the import of the ADMX/ADML files into intune.
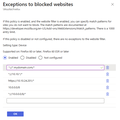
Having read https://support.mozilla.org/en-US/kb/managing-firefox-intune I have set '\Mozilla\Firefox\Exceptions to blocked websites' to the following; //*.mydomain.com/*
Which works, however, I also want to add hosts that are only resolving on IPs and not DNS. I can add specific IPs if known, but is there a way I can allow IP ranges? Ie
//10.10.*/* (this doesn't currently work) Of the included screenshot, only the wildcard for mydomain.com and the specific IP currently work
I've looked over the link that is recommened in the policy (indirectly) and can't see an option for allowing an IP range. https://developer.mozilla.org/en-US/docs/Mozilla/Add-ons/WebExtensions/Match_patterns
If there is a better way to do this via intune for firefox only, please let me know.
Thanks
被采纳的解决方案
We've kind of got this to work, and it appears to be (with the other setttings) blocking access to sites not defined by DNS or IP range
Proxy Passthrough \Mozilla\Firefox\Proxy Settings 10.0.0.0/8, http:/domain.com/* , <local>
HTTP Proxy
\Mozilla\Firefox\Proxy Settings > enabled
127.0.0.1:80
HTTPS Proxy \Mozilla\Firefox\Proxy Settings > enabled 127.0.0.1:443
定位到答案原位置 👍 0所有回复 (3)
Are those sites navigated to by IP address or by name?
Mike Kaply said
Are those sites navigated to by IP address or by name?
We have some internal sites that have resolvable DNS, so can be reached on the internal domain, this section of the 'exceptions to blocked sites' does work. Adding the full internal IP to the 'exceptions to blocked sites' also works, but unfortunately its not too manageable to add all individual IPs to the list, which is why I would like to add an internal range ie 10.0.0.0 /16 or similar. As you may see from the screenshot, I've tried a few variations, but these are not working
Thanks
选择的解决方案
We've kind of got this to work, and it appears to be (with the other setttings) blocking access to sites not defined by DNS or IP range
Proxy Passthrough \Mozilla\Firefox\Proxy Settings 10.0.0.0/8, http:/domain.com/* , <local>
HTTP Proxy
\Mozilla\Firefox\Proxy Settings > enabled
127.0.0.1:80
HTTPS Proxy \Mozilla\Firefox\Proxy Settings > enabled 127.0.0.1:443
由matthew89于