wildcard certificate is not validated when using ssl proxy
Hello,
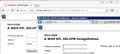
I am managing a corporate netowork, we have an ssl proxy on the gateway (Juniper SRX), bridgeing ssl connections to the internet. All client comuter trust in the CA of the gateway, who replaces certifiactes on the fly. I directed Firefox to use the Computer's CA Store what contains the root CA of the gateway as trusted. All Internet connections are fine from Firefox except the sites that are using wildcard certificates. In that case we receive SEC_ERROR_UNKNOWN_ISSUER error. When investigating the certificate we see that SSL-PROXY:DUMMY_CERT:GENERATED DUE TO SRVR AUTH FAILURE is in the CN. All other browsers handling fine the wildcard certificates in the same environment. Adding exception is not a solution since there are many wildcard certificates.
Thanks, Balázs
由bbajmoczi于
所有回复 (5)
Is there any security software involved on your clients, and did you read the Troubleshoot security error codes on secure websites support article?
Hello,
I can say that there is no other software on the clients that influenses this issue. Yes, I read that article, and I am really aware of this error. That article is not close to my problem. I quote :"In case you get this problem on multiple unrelated HTTPS-sites, it indicates that something on your system or network is intercepting your connection and injecting certificates in a way that is not trusted by Firefox. The most common causes are security software scanning encrypted connections or malware listening in, replacing legitimate website certificates with their own" Yes a security software is scanning content. But I installed the root CA of the security software, what is running on the SSL proxy.
The installed certificate is working fine, until the site that the client visits not using a wildcard certificate.
bbajmoczi said
I directed Firefox to use the Computer's CA Store what contains the root CA of the gateway as trusted. All Internet connections are fine from Firefox except the sites that are using wildcard certificates. In that case we receive SEC_ERROR_UNKNOWN_ISSUER error. When investigating the certificate we see that SSL-PROXY:DUMMY_CERT:GENERATED DUE TO SRVR AUTH FAILURE is in the CN.
Maybe this is a limitation of the security.enterprise_roots.enabled = true workaround. I haven't researched the documentation on exactly how it works.
If you set that back to false and instead add the proxy's signing certificate as an authority certificate in Firefox -- the traditional workaround -- does that work? The steps for that are in this thread: sec_error_bad_signature only via proxy for https website. Note: with the reorganization of the Options page in Firefox 56+, you may find it fastest to put cert in the search box at the top of the page to find the View Certificates button.
Hello Jscher,
thanks for your reply. Yes, in the traditional way it works fine, If I add the root CA of the proxy to Firefox, both wildcard and normal certificates are fine.
The problem is that I have several hunderds of clients and there is no way to automate the certificate import to Firefox.
With the corporate mangement tool I changed Firefox to use the computer's store where I already deployed this root CA.
Yes, it look like a limitation...
由bbajmoczi于
I suggest filing a bug for this, or searching for a bug on file. It probably is intended to support your scenario, but developers may need assistance from a current user to work out and test a fix.