Firefox chooses wrong TLS version
When connecting to our webmail site, Firefox chooses to use TLS 1.1. On recent Firefox versions this will require lowering the security.tls.version.fallback-limit to 2 to allow the connection.
If I use Chrome, it will use TLS 1.2
I checked all I could think of on the webserver but wasn't able to find the problem.
The website is https://mdmail.enteautonomovolturno.it (we use our private CA, if you want you can download the certs from http://assistenza.enteautonomovolturno.it/downloads/ca_eav.zip )
Any suggestion?
ప్రత్యుత్తరాలన్నీ (8)
Hello!
This issue is affecting all browsers including Chrome. The main cause is the browser does not know who the "insurer" of this certificate is
The reason for your problem:
"The certificate is not signed by a trusted authority (checking against Mozilla's root store). If you bought the certificate from a trusted authority, you probably just need to install one or more Intermediate certificates. Contact your certificate provider for assistance doing this for your server platform."
I already added the CA certficate to the system store and to the mozilla firefox internal store. Chrome browse the site just fine, as does Firefox when allowing TLS 1.1 in the config.
The website may try to fallback to TLS 1.0 in a way that is no longer allowed in current releases or may be using a deprecated cipher suite.
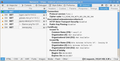
You can open the about:config page via the location/address bar and use its search bar to locate this pref:
- security.tls.insecure_fallback_hosts
You can double-click the line to modify the pref and add the full domain (TEXT) to the value of this pref. If there are already websites (domains) in this list then add a comma and the new domain (no spaces). There should only be domains separated by a comma in the Value column (example.com,www.example.com).
If this helps then you can contact this website and ask them to look into this and update their security.
I'm not looking for workarounds, I already know that two (the fallback limit and the fallback hosts list). I'm the one who runs the webserver. I'm trying to understand why Firefox isn't using TLS 1.2, as it is enabled on the webserver and 1) Chrome is using it! 2) Tests with https://www.ssllabs.com/ssltest/analyze.html?d=webmail.enteautonomovolturno.it reports TLS 1.2 is active
When running tests with qualsys tools, please keep in mind this is a Private CA certificate so some tests will obviuosly fail
Bye
Hello!
From whoever you bought this SSL certificate from I strongly suggest contacting them or in a better case contact whoever is hosting your website such as godaddy, hostgator etc etc
As I already said "we use our private CA". The certificate is fine for chrome, internet explorer and, apart from being emitted by an unknown CA, for ssllabs tests.
Bye
Works for me if I install the root certificate and set the trust bit for websites.
I need to add the website to the whitelist like I posted above to bypass the security error. Firefox uses TLS 1.1 and TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
And that's the issue. Firefox needs to add the exception to the config (or allow to fallback to tls 1.1) because it cannot establish a tls 1.2 connection, like Chrome DOES. These is some issue with the handshake and I'm trying to determine if I can solve it or is some kind of incompatibility. The website it's a webmail and I've got a lot of users that could possibly browse it with Firefox. No way I'll tell them to change the config... if I can't solve the problem I'll just declare Firefox as unsupported for our website.
Bye