Exempt domains/urls from add-on/extensions?
After the recent reveal about ad block plus filters gaining unauthorized access to privileged information, and a further discussion at work about how we can protect ourselves from future add-ons/extensions doing something similar, I thought one possible solution could be to configure the web browser to exempt certain urls/domains from all add-ons.
For instance, say I wanted to protect my gmail content. I could add mail.google.com to this list so that Firefox wouldn't let any add-on see the content coming from or to it.
Does Firefox have something like this already? Or is there an add-on that proxies add-ons with Firefox that can do this?
Toutes les réponses (6)
One option -- not especially convenient -- is to add the site to the restricted domains list. That's a list of sites where even if the extension normally would have host permission on a listed site, the extension will not be able to take any actions on that site that require host permission. It's most obvious with content scripts not being injected into pages, but also affects methods that modify requests.
This is how extensions are blocked from accessing content on the Mozilla Add-ons site, for example.
If you want to try it:
(1) In a new tab, type or paste about:config in the address bar and press Enter/Return. Click the button promising to be careful or accepting the risk.
(2) In the search box above the list, type or paste restr and pause while the list is filtered
(3) Double-click the extensions.webextensions.restrictedDomains preference to display a dialog where you can edit the value. Then:
(A) Click at the start or press the Home key to move the cursor to the beginning of the value
(B) Type or paste the new host name (for example, www.userchrome.org) at the beginning of the list, then type a comma to separate it from the original first item, without adding any extra spaces.
(C) Click OK to save.
If the value gets mucked up, right-click the preference and choose Reset to restore the factory list.
Since it can be dangerous for users to remove Mozilla sites from the list -- some of those sites have elevated access to browser data -- editing this preference is not recommended. However, as I don't think there is an alternative at the moment, if there's a site you really need to browse unmodified, it a list you could add to until a better option comes along.
Modifié le
Thanks for this, it's an interesting setting.
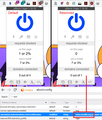
I gave it a try -- it does prevent the extension from modifying the page, however it looks like the extension can still see all of the content on the page. I used ublock origin as the test -- it showed that it blocked a high number of things when I visited a particular site that was added to the restrictedDomains preference, however all the ads showed up, so the page wasn't actually modified.
What I was hoping to see was ublock origin with the counter set to 0 -- showing that it never saw the content of the site.
You could ask the author what is going on. Maybe the extension sees all the third party site requests generated by the page (because it is allowed to see those), and thinks it is blocking them, but it can't actually do it. https://www.reddit.com/r/uBlockOrigin/
The goal is to have a list sites that can't be touched (read or write) by any extension since I have no way to validate that extensions are safe from abuse.
I.E. give my users the ability to load any extension they want, as long as those extensions can't touch work-related sites. The alternative is to block all extensions. :(
I understand the goal, and it should work. If it doesn't work, there's a bug. When I test using www.mozilla.org as the domain, it seems to work normally. I am attaching a screenshot for reference.
Heh, looks like Mozilla took care of my extension problem a different way :)
I'll have to wait until they fix that cert problem before I can check on this again.
The test I ran was on Ubuntu btw -- I won't have access to that machine again until Monday, but I can try some tests at home from Windows and macOS to see if the behavior is any different. I'll provide screenshots too.