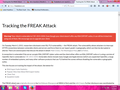
Using FF 36 but still getting message on testing for vulnerability for "Freak" hack.
"Warning! Your client is vulnerable to CVE-2015-0204. Even though your client doesn't offer any RSA EXPORT suites, it can still be tricked into using one of them. We encourage you to upgrade your client. "
Chosen solution
https://nakedsecurity.sophos.com/2015/03/04/the-freak-bug-in-tlsssl-what-you-need-to-know/
"As far as we know, the trick doesn't work against the TLS implementations used by Microsoft, Google and Mozilla.
So users of Internet Explorer, Chromium/Chrome and Firefox are OK."
This pretty much just affects default browser Android users on old versions of Android, Safari users, and old and out of date browsers. Users using Firefox 36 as safe against this attack (at least, as far as it is currently understood)
Read this answer in context 👍 1All Replies (12)
Chosen Solution
https://nakedsecurity.sophos.com/2015/03/04/the-freak-bug-in-tlsssl-what-you-need-to-know/
"As far as we know, the trick doesn't work against the TLS implementations used by Microsoft, Google and Mozilla.
So users of Internet Explorer, Chromium/Chrome and Firefox are OK."
This pretty much just affects default browser Android users on old versions of Android, Safari users, and old and out of date browsers. Users using Firefox 36 as safe against this attack (at least, as far as it is currently understood)
which security software are you running on the pc?
Where did you do this test? I would be very cautious of fake sites popping up on the crisis du jour that want to infect you with whatever they're peddling.
Firefox 36.0 on Windows 7 and on Android 4.4 are both passing for me on that site.
Tyler Downer said
https://nakedsecurity.sophos.com/2015/03/04/the-freak-bug-in-tlsssl-what-you-need-to-know/ "As far as we know, the trick doesn't work against the TLS implementations used by Microsoft, Google and Mozilla. So users of Internet Explorer, Chromium/Chrome and Firefox are OK." This pretty much just affects default browser Android users on old versions of Android, Safari users, and old and out of date browsers. Users using Firefox 36 as safe against this attack (at least, as far as it is currently understood)
Thank you for your reply and efforts. But I am curious that why freak attack is saying that on my testing? I am attaching screen shot.
And i am using Avast internet security.
then your antivirus software is actually making you less secure when it starts fiddling with https connections instead of leaving that to the browser, as has been discovered by this user as well: https://support.mozilla.org/en-US/questions/1050149#answer-699259
edit: avast had issues with the poodle vulnerability as well: https://forum.avast.com/index.php?topic=161458.0
Modified
Avast is pretty crap. You are better off with this as security:
- Use Microsoft Security Essentials+Windows default Firewall
- Keep Windows up to date
- Keep Firefox and all plugins up to date
- Run malwarebytes on a regular basis (once a month, unless you want to be more frequent).
Uninstall Avast.
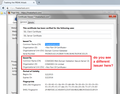
Hi Uzairn91, if you click the padlock icon for the site, then More Information, then View Certificate, what issuer do you see? I have attached what I believe is the normal information. If you see a different issuer, then avast! or something else probably is proxying your connection.
Tyler Downer said
Avast is pretty crap. You are better off with this as security:Uninstall Avast.
- Use Microsoft Security Essentials+Windows default Firewall
- Keep Windows up to date
- Keep Firefox and all plugins up to date
- Run malwarebytes on a regular basis (once a month, unless you want to be more frequent).
You are right but let me tell you that Avast has saved me from dozens of online trojans and attacks.. Above settings are not very good in my point of view. But thanks for putting up efforts and helping me out.
@all
Thank you everyone! Issue resolved. Culprit was avast.
jscher2000 is right. Avast is playing with my certificates.
I had my definitions of avast already updated last night when i tested for freak hack. Just now I updated avast definitions and also there was program update, which i did also. After that tests result are good. I am no more vulnerable to freak.
Anyone having same problem, solution = update definitions and program both of your avast.