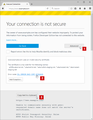
incomprehensible: "www.google.com uses an invalid security certificate. You have to be kidding. Right!? "
When searching Google, the response below is frequently displayed and Google is blocked. Exception option is NOT displayed when "Advance" is selected, as seen below. (FYI: No amount of research has yielded a permanent fix. Downgrade to ver 46.0.1 was fine for sometime, then it broke. Ver 20 does not have this problem; but has other serious security issues. OS: Win 7 Pro SP1. Asus i3 64-bit 4Gb)
"Your connection is not secure
The owner of www.google.com has configured their website improperly. To protect your information from being stolen, Firefox has not connected to this website.
This site uses HTTP Strict Transport Security (HSTS) to specify that Firefox only connect to it securely. As a result, it is not possible to add an exception for this certificate.
Learn more…
Report errors like this to help Mozilla identify misconfigured sites
www.google.com uses an invalid security certificate.
The certificate is not trusted because the issuer certificate is unknown. The server might not be sending the appropriate intermediate certificates. An additional root certificate may need to be imported.
Error code: SEC_ERROR_UNKNOWN_ISSUER"
Valgt løsning
Thank u again philipp.
After some further digging, the issue was sidestepped by editing the link to google in the bookmark. That link was obtained by bookmarking google using the standard bookmark star in Frfx. It used to read https://www.google.com/?gfe_rd=cr&ei=F_18VtzbBoqx8weY9YbIAg&gws_rd=cr&fg=1
Now it reads, simply: https://www.google.com/ncr
BTW. I use /ncr to keep google from defaulting to local pages.
HTTPS port 443 scanning by Kaspersky was restored before using the bookmark. I restarted between changes to AV settings.
There were too many indicators the issue had nothing to do with how Kaspersky deals with HTTPS scanning. The most significant is that other HTTPS sites are accessed without a hitch.
The issue seems to result from the address suffix which google added when the bookmark was set. No clue what that string triggered nor why it was added in the first place. Does not matter. Now we have further proof, KISS works.
Your guidance and patience is most kindly appreciated.
Issue is resolved,
Læs dette svar i sammenhæng 👍 3Alle svar (12)
Please see this support page: https://support.mozilla.org/en-US/kb/troubleshoot-SEC_ERROR_UNKNOWN_ISSUER
Thank you edmeister. Been there, tried that. Doesn't work. Repeated again coz you kindly took the time to suggest. Still same problem. FYI: AV Kasp Internet 2015.
PS: After posting above, logged into gmail account through Firefox to see what might happen. Sure thing, problem went away. Seems issue is in some pre-search "handshake" with Google which is resolved by login to a Google account. Well, I DO NOT wish to login to our friendly giant while I do work which has nothing to do with my gmail account. To that end, I am prepared to switch to Opera or others (NOT Chrome).
Please help fix this. Firefox is too valuable. Many thanks.
Ændret af MHMM den
You should realise I; and I am sure most people; do not see this sort of issue. It is almost definitely caused by your security software fighting with Firefox. Just temporarily try disabling your Kaspersky software does Firefox then work as expected ? If it does not then temporarily remove the Kaspersky software. (Some security software has effects and interactions even when apparently disabled)
Firefox is not going to insist you log in to Google Accounts. If you do not like Google's snooping and avoid Google Chrome then maybe you should consider not using their Search engine (& for that matter not using their webmail).
The issue might have not been noted - or not reported - for any number of reasons. Regardless of such, the combination of Kaspersky, Firefox and Google search are significant tools for many on the scale of today's web use. The connection to my webmail choice was reported as additional information for consideration in understanding the behavior of that combination. Just so the picture is complete, the reported issue is intermittent.
We all understand that a site such as Google is not going to be using an invalid certificate. The problem is almost certainly with your own computer's setup.
You either have malware of something intercepting and interfering with your connection, or possibly your ISP has problems but far more likely security software is not set up to work properly with Firefox. When that happens you may try to work round the problems by setting exceptions, but will run in to similar problems every time a new secure link is used either directly because of what you key in, or indirectly because of the content or scripts of a particular site.
Did you try disabling Kaspersky ? Did you try temporarily uninstalling it ? Probably more relevant did you carefully read and try the instructions in:
In Kaspersky security products you can disable the interception of secure connections:Those are the instructions Ed has already suggested you try.
- Open the dashboard of your Kaspersky application.
- Click on {menu Settings} on the bottom-left.
- Click {menu Additional} and then {menu Network}.
- If you use a 2016 version of Kaspersky: In the {menu Encrypted connections scanning} section check the {pref Do not scan encrypted connections} option and confirm this change.
Alternatively you can click on {menu Advanced Settings} in order to try to trigger a reinstallation of Kaspersky's certificate. In the dialog that opens click on {button Install certificate…} and follow the on-screen instructions.
If you use a 2015 version of Kaspersky: uncheck the {pref Scan encrypted connections} option.- Finally, reboot your system for the changes to take effect.
Users of an earlier version of Kaspersky with a current subscription are entitled to an upgrade to the latest product version, which is available for download and installation on the Kaspersky product updates page. Afterwards follow the steps from above.
The issue was first noted when Frfx auto updated to ver 47. Prior to posting, the typical instructions were followed, including those specific to Kaspersky. That did not resolve it. The process was repeated when Ed kindly suggested it. As reported earlier, no luck. The issue is NOT related to conflicts between Frfx and the AV. Several indicators point to that. Thus, no attempt at disabiling or re-moving and re-installing the AV shall be undertaken. Neither is it related to problems with the ISP. Several are used and it still shows up with same frequency. Nor is it related to possible malware. None exists. This person is obsessive about safe everything, follows up with routine scans and weary about unusual behaviours. I shall figure out exactly where the issue is, and the finding will be posted. Debugging is not rocket science. It lives in the meticulous pursuit of detail. No replies to this post are indicated. It is presented for the interest of those seeking to learn what causes things possibly unseen before. Peace !
please give us more information about the error by clicking on the error code, copying the text to the clipboard and then pasting it here into a reply in the forum.
thank you!
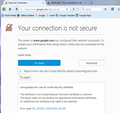
Thank u philipp. Just tried again. This time the error message included option to add exception. Screen print attached as jpg. Next is copy of error code. BTW, I linked to Google through bookmark.
https://www.google.com/?gfe_rd=cr&ei=F_18VtzbBoqx8weY9YbIAg&gws_rd=cr&fg=1
Peer's Certificate issuer is not recognized. HTTP Strict Transport Security: false HTTP Public Key Pinning: false
Certificate chain:
BEGIN CERTIFICATE-----
MIIDjTCCAnWgAwIBAgIMeNmCa99DlHrNAuT/MA0GCSqGSIb3DQEBCwUAMFUxGjAYBgNVBAoMEUthc3BlcnNreSBMYWIgWkFPMTcwNQYDVQQDDC5LYXNwZXJza3kgQW50aS1WaXJ1cyBQZXJzb25hbCBSb290IENlcnRpZmljYXRlMB4XDTE2MDkwNzIzMzgxNloXDTE2MTEzMDIzMzEwMFowaDELMAkGA1UEBhMCVVMxEzARBgNVBAgMCkNhbGlmb3JuaWExFjAUBgNVBAcMDU1vdW50YWluIFZpZXcxEzARBgNVBAoMCkdvb2dsZSBJbmMxFzAVBgNVBAMMDnd3dy5nb29nbGUuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAxYJWbS0Vz1u7SCG1OeH0q032Q6sVFzE3OJiaHeNnSdLelaaXiK/NiFKd2vVm6t12nFcfwa+yb/eb17CD7V62R2zj/80mmnmgYsLBtqXoAFs1tqJWJtp1DdhrYZLK1Cf4AGKaSCrBKJjsM5NjqWL4n9ff0uhD0uJXrZniOswUUUzwwjl+5FRVOU7n06VuWMr6JFUAT/2o4CvniHB0TyKS1x+ZSbT6jxKmoISS9hCgkhf+WNSfmLM54Cf+0oa4bm4Q2W2YIEhJC0cVwdwLTf75US5meYyLPz2sotcjunxMK5ppusujhf/XNzIuO2H1Yxw597JVEifNn4Q8EvXl4S8smQIDAQABo0owSDAZBgNVHREEEjAQgg53d3cuZ29vZ2xlLmNvbTAMBgNVHRMBAf8EAjAAMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjANBgkqhkiG9w0BAQsFAAOCAQEAO3qrr8koJlgeWvhkC8bQhF3yyFtTvjN1kWphLQEk/euOseeh1/MjoFlCvctl3nDmG3xf+amn//Sbuh3N7kmVmtbMgyDWqkkloc3JB28gRd1DoVwTgXXLI4XCNaqp3Hboe0DkT/KjaNUGt0anbjsiWOTaIUUEug6nxIHZoDtkIxyCMr03JgQijXHyHA03elnfg2N7UddhGw4iXTkqSVx68hwNWecH8PfXT5ICx48PWhMNRsEIn3CIqTfaWk5DeOM0sY9zc7PyNibGFUBo36z0Sc+j9eNP79rhPyKhMGldIQSF9D5gjwTAApuitGHbTXzB9NIvJCnlscfQ+UtveRoYOA==
END CERTIFICATE-----
BEGIN CERTIFICATE-----
MIIDQDCCAiigAwIBAgIJAKn801dmrjK1MA0GCSqGSIb3DQEBCwUAMFUxGjAYBgNVBAoMEUthc3BlcnNreSBMYWIgWkFPMTcwNQYDVQQDDC5LYXNwZXJza3kgQW50aS1WaXJ1cyBQZXJzb25hbCBSb290IENlcnRpZmljYXRlMB4XDTE2MDkxMDEyMjkyOVoXDTI2MDkwODEyMjkyOVowVTEaMBgGA1UECgwRS2FzcGVyc2t5IExhYiBaQU8xNzA1BgNVBAMMLkthc3BlcnNreSBBbnRpLVZpcnVzIFBlcnNvbmFsIFJvb3QgQ2VydGlmaWNhdGUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDFglZtLRXPW7tIIbU54fSrTfZDqxUXMTc4mJod42dJ0t6VppeIr82IUp3a9Wbq3XacVx/Br7Jv95vXsIPtXrZHbOP/zSaaeaBiwsG2pegAWzW2olYm2nUN2GthksrUJ/gAYppIKsEomOwzk2OpYvif19/S6EPS4letmeI6zBRRTPDCOX7kVFU5TufTpW5YyvokVQBP/ajgK+eIcHRPIpLXH5lJtPqPEqaghJL2EKCSF/5Y1J+YszngJ/7ShrhubhDZbZggSEkLRxXB3AtN/vlRLmZ5jIs/Payi1yO6fEwrmmm6y6OF/9c3Mi47YfVjHDn3slUSJ82fhDwS9eXhLyyZAgMBAAGjEzARMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEBAIMcuoQCDdYY2wc5Z1js0Qyr9rizvV2BdBvQQE8il4YK2PLOY7NTD4OaoBq/1/E81U4sn9c16xumSGZWNGgz065ASY1/XxfXeW8SjXpvUeyjbxKjI75VUsDTYyfyXxNMyfbRG/0pTAGjodd5uYLJb0njp/5i6KicPcobfeXREgQSoKXTVKFxuvr3FexLvisg3y6vqAsFbDO9dh4CjLlEShpWtR4nGFZojF+Tg0pb1LodFT0f3VcfqPOAs1O+66dOhYLp8/ZiFc+bAvqCfm1YAuNTqePvEq2j8P8X3q8SB1EeQI5dINeX89PFz5jqX8iUaWshYdLGeQHCxLJEQtU9D1s=
END CERTIFICATE-----
thanks, that is showing that it IS Kaspersky Anti-Virus Personal Root Certificate which is used to intercept your secure connections - so i strongly recommend that you turn of HTTPS scanning within its settings.
Thanks. Encrypted connections scanning was already turned off. To turn off HTTPS scanning, port 443 was made "Inactive". That is found under "Monitored ports". That did not help as you can see below. I will dig some more and let you know.
https://www.google.com/?gfe_rd=cr&ei=F_18VtzbBoqx8weY9YbIAg&gws_rd=cr&fg=1
Peer's Certificate issuer is not recognized.
HTTP Strict Transport Security: true HTTP Public Key Pinning: false
Certificate chain:
BEGIN CERTIFICATE-----
MIIDjTCCAnWgAwIBAgIMeNmCa99DlHrNAuT/MA0GCSqGSIb3DQEBCwUAMFUxGjAY BgNVBAoMEUthc3BlcnNreSBMYWIgWkFPMTcwNQYDVQQDDC5LYXNwZXJza3kgQW50 aS1WaXJ1cyBQZXJzb25hbCBSb290IENlcnRpZmljYXRlMB4XDTE2MDkwNzIzMzgx NloXDTE2MTEzMDIzMzEwMFowaDELMAkGA1UEBhMCVVMxEzARBgNVBAgMCkNhbGlm b3JuaWExFjAUBgNVBAcMDU1vdW50YWluIFZpZXcxEzARBgNVBAoMCkdvb2dsZSBJ bmMxFzAVBgNVBAMMDnd3dy5nb29nbGUuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOC AQ8AMIIBCgKCAQEAxYJWbS0Vz1u7SCG1OeH0q032Q6sVFzE3OJiaHeNnSdLelaaX iK/NiFKd2vVm6t12nFcfwa+yb/eb17CD7V62R2zj/80mmnmgYsLBtqXoAFs1tqJW Jtp1DdhrYZLK1Cf4AGKaSCrBKJjsM5NjqWL4n9ff0uhD0uJXrZniOswUUUzwwjl+ 5FRVOU7n06VuWMr6JFUAT/2o4CvniHB0TyKS1x+ZSbT6jxKmoISS9hCgkhf+WNSf mLM54Cf+0oa4bm4Q2W2YIEhJC0cVwdwLTf75US5meYyLPz2sotcjunxMK5ppusuj hf/XNzIuO2H1Yxw597JVEifNn4Q8EvXl4S8smQIDAQABo0owSDAZBgNVHREEEjAQ gg53d3cuZ29vZ2xlLmNvbTAMBgNVHRMBAf8EAjAAMB0GA1UdJQQWMBQGCCsGAQUF BwMBBggrBgEFBQcDAjANBgkqhkiG9w0BAQsFAAOCAQEAO3qrr8koJlgeWvhkC8bQ hF3yyFtTvjN1kWphLQEk/euOseeh1/MjoFlCvctl3nDmG3xf+amn//Sbuh3N7kmV mtbMgyDWqkkloc3JB28gRd1DoVwTgXXLI4XCNaqp3Hboe0DkT/KjaNUGt0anbjsi WOTaIUUEug6nxIHZoDtkIxyCMr03JgQijXHyHA03elnfg2N7UddhGw4iXTkqSVx6 8hwNWecH8PfXT5ICx48PWhMNRsEIn3CIqTfaWk5DeOM0sY9zc7PyNibGFUBo36z0 Sc+j9eNP79rhPyKhMGldIQSF9D5gjwTAApuitGHbTXzB9NIvJCnlscfQ+UtveRoY OA==
END CERTIFICATE-----
BEGIN CERTIFICATE-----
MIIDQDCCAiigAwIBAgIJAKn801dmrjK1MA0GCSqGSIb3DQEBCwUAMFUxGjAYBgNV BAoMEUthc3BlcnNreSBMYWIgWkFPMTcwNQYDVQQDDC5LYXNwZXJza3kgQW50aS1W aXJ1cyBQZXJzb25hbCBSb290IENlcnRpZmljYXRlMB4XDTE2MDkxMDEyMjkyOVoX DTI2MDkwODEyMjkyOVowVTEaMBgGA1UECgwRS2FzcGVyc2t5IExhYiBaQU8xNzA1 BgNVBAMMLkthc3BlcnNreSBBbnRpLVZpcnVzIFBlcnNvbmFsIFJvb3QgQ2VydGlm aWNhdGUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDFglZtLRXPW7tI IbU54fSrTfZDqxUXMTc4mJod42dJ0t6VppeIr82IUp3a9Wbq3XacVx/Br7Jv95vX sIPtXrZHbOP/zSaaeaBiwsG2pegAWzW2olYm2nUN2GthksrUJ/gAYppIKsEomOwz k2OpYvif19/S6EPS4letmeI6zBRRTPDCOX7kVFU5TufTpW5YyvokVQBP/ajgK+eI cHRPIpLXH5lJtPqPEqaghJL2EKCSF/5Y1J+YszngJ/7ShrhubhDZbZggSEkLRxXB 3AtN/vlRLmZ5jIs/Payi1yO6fEwrmmm6y6OF/9c3Mi47YfVjHDn3slUSJ82fhDwS 9eXhLyyZAgMBAAGjEzARMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQELBQAD ggEBAIMcuoQCDdYY2wc5Z1js0Qyr9rizvV2BdBvQQE8il4YK2PLOY7NTD4OaoBq/ 1/E81U4sn9c16xumSGZWNGgz065ASY1/XxfXeW8SjXpvUeyjbxKjI75VUsDTYyfy XxNMyfbRG/0pTAGjodd5uYLJb0njp/5i6KicPcobfeXREgQSoKXTVKFxuvr3FexL visg3y6vqAsFbDO9dh4CjLlEShpWtR4nGFZojF+Tg0pb1LodFT0f3VcfqPOAs1O+ 66dOhYLp8/ZiFc+bAvqCfm1YAuNTqePvEq2j8P8X3q8SB1EeQI5dINeX89PFz5jq X8iUaWshYdLGeQHCxLJEQtU9D1s=
END CERTIFICATE-----
if you put that certificate information into a tool like https://certlogik.com/decoder/ to make it human-readable you'll see that kaspersky is still involved in the issue. if just disabling the option to scan secure connections doesn't work, i'd recommend to get in contact with their support about it, or else try to uninstall (you might test it right afterwards) and reinstall kaspersky...
Valgt løsning
Thank u again philipp.
After some further digging, the issue was sidestepped by editing the link to google in the bookmark. That link was obtained by bookmarking google using the standard bookmark star in Frfx. It used to read https://www.google.com/?gfe_rd=cr&ei=F_18VtzbBoqx8weY9YbIAg&gws_rd=cr&fg=1
Now it reads, simply: https://www.google.com/ncr
BTW. I use /ncr to keep google from defaulting to local pages.
HTTPS port 443 scanning by Kaspersky was restored before using the bookmark. I restarted between changes to AV settings.
There were too many indicators the issue had nothing to do with how Kaspersky deals with HTTPS scanning. The most significant is that other HTTPS sites are accessed without a hitch.
The issue seems to result from the address suffix which google added when the bookmark was set. No clue what that string triggered nor why it was added in the first place. Does not matter. Now we have further proof, KISS works.
Your guidance and patience is most kindly appreciated.
Issue is resolved,